Blockchain Oracle Development: A Complete Guide for Smart Contract Integration
Smart contracts changed how agreements run online. There’s one big gap, though: blockchains do not fetch outside data by themselves. That limitation created an entire discipline blockchain oracle development and it now sits at the heart of serious dApp work.
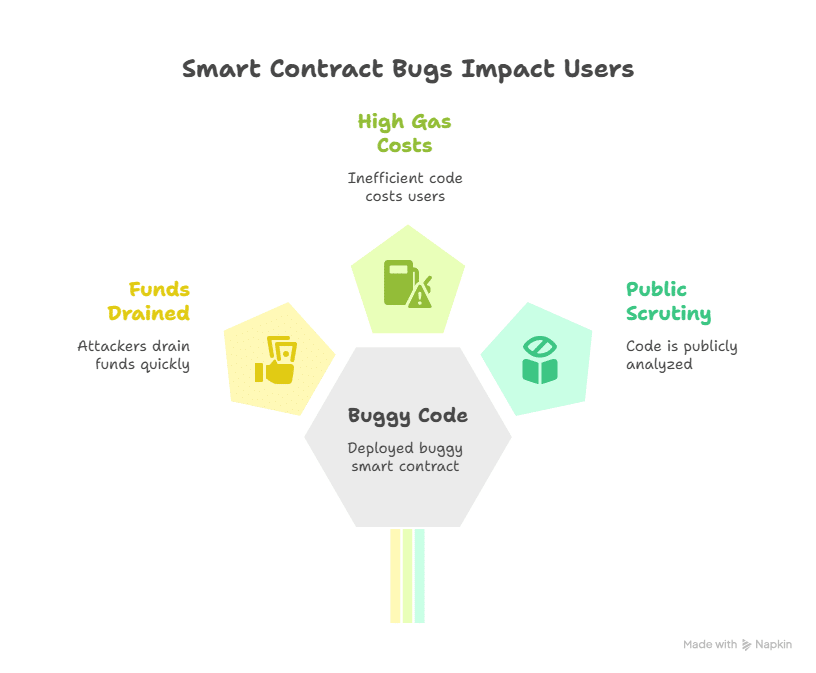
Think through a few common builds. A lending protocol needs live asset prices. A crop-insurance product needs verified weather. An NFT game needs randomness that players cannot predict. None of that works without an oracle. Get the oracle piece wrong and you invite price shocks, liquidations at the wrong levels, or flat-out exploits.
This guide lays out the problem, the tools, and the practical moves that keep your contracts safe while still pulling the real-world facts you need.
The Oracle Problem: Why Blockchains Can’t Talk to the Real World
Blockchains are deterministic and isolated by design. Every node must reach the same result from the same inputs. That’s perfect for on-chain math, and terrible for “go ask an API.” If a contract could call random endpoints, nodes might see different responses and break consensus.
That creates the classic oracle problem: you need outside data, but the moment you trust one server, you add a single point of failure. One feed can be bribed, hacked, or just go down. Now a supposedly trust-minimised system depends on one party.
The stakes are higher in finance. A bad price pushes liquidations over the edge, drains pools, or lets attackers walk off with funds. We’ve seen it. The fix isn’t “don’t use oracles.” The fix is to design oracles with clear trust assumptions, meaningful decentralisation, and defenses that trigger before damage spreads.
Types of Blockchain Oracles You Should Know
Choosing the right fit starts with a quick model map. These types of blockchain oracles for dApps cover most needs:
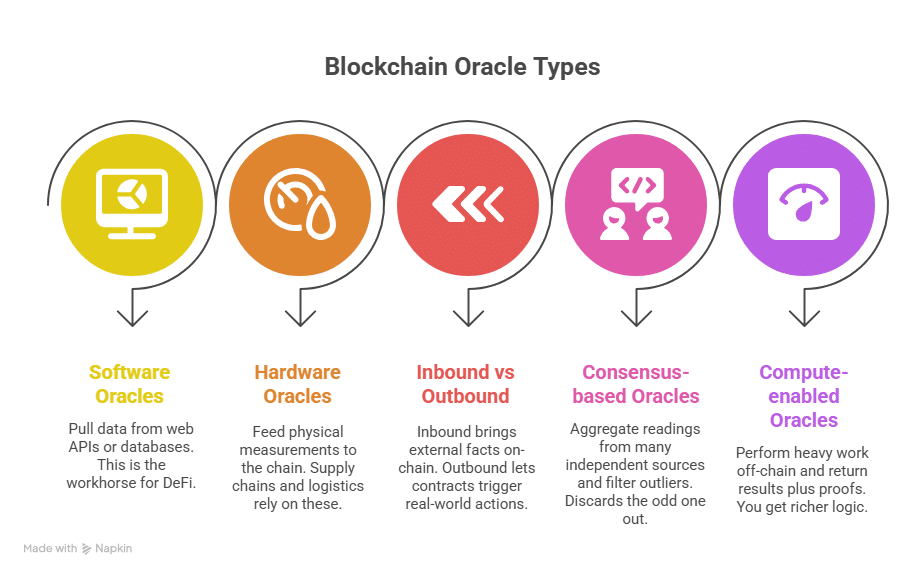
1) Software oracles
Pull data from web APIs or databases: asset prices, sports results, flight delays, shipping status. This is the workhorse for DeFi, prediction markets, and general app data.
2) Hardware oracles
Feed physical measurements to the chain: GPS, temperature, humidity, RFID events. Supply chains, pharmaceutical cold chains, and logistics rely on these.
3) Inbound vs Outbound
- Inbound: bring external facts on-chain so contracts can act.
- Outbound: let contracts trigger real-world actions — send a webhook, start a payment, ping a device.
4) Consensus-based oracles
Aggregate readings from many independent sources and filter outliers. If four feeds say $2,000 and one says $200, the system discards the odd one out.
5) Compute-enabled oracles
Perform heavy work off-chain (randomness, model inference, large dataset crunching) and return results plus proofs. You get richer logic without blowing up gas.
Centralized vs. Decentralized: Picking an Oracle Model That Matches Risk
This choice mirrors broader blockchain tradeoffs.
Centralized oracles
- Pros: fast, simple, low overhead, good for niche data.
- Cons: single operator, single failure path. If it stops or lies, you’re stuck.
Decentralized oracle networks
- Pros: many nodes and sources, aggregation, cryptoeconomic pressure to behave, resilience under load.
- Cons: higher cost than one server, a bit more latency, and more moving parts.
A good rule: match the design to the blast radius. If the data touches balances, liquidations, or settlements, decentralize and add fallbacks. If it powers a UI badge or a leaderboard, a lightweight source can be fine.
Hybrid is common: decentralized feeds for core money logic, lighter services for low-stakes features.
Top Oracle Providers (What They’re Best At)
Choosing from the best Oracle providers for blockchain developers requires understanding each platform’s strengths and ideal use cases. Here’s what you need to know about the major players.
Chainlink: The Industry Standard
Chainlink dominates the space for good reason. It’s the most battle-tested, most widely integrated oracle network, supporting nearly every major blockchain. Chainlink offers an impressive suite of services: Data Feeds provide continuously updated price information for hundreds of assets; VRF (Verifiable Random Function) generates provably fair randomness for gaming and NFTs; Automation triggers smart contract functions based on time or conditions; CCIP enables secure cross-chain communication.
The extensive documentation, large community, and proven track record make Chainlink the default choice for many projects. Major DeFi protocols like Aave, Synthetix, and Compound rely on Chainlink price feeds. If you’re unsure where to start, Chainlink is usually a safe bet.
Band Protocol: Cost-Effective Speed
Band Protocol offers a compelling alternative, particularly for projects prioritizing cost efficiency and speed. Built on Cosmos, Band uses a delegated proof-of-stake consensus mechanism where validators compete to provide accurate data. The cross-chain capabilities are excellent, and transaction costs are notably lower than some alternatives. The band has gained traction, especially in Asian markets and among projects requiring frequent price updates without excessive fees.
API3: First-Party Data Connection
API3 takes a fascinating first-party approach that eliminates middlemen. Instead of oracle nodes fetching data from APIs, API providers themselves run the oracle nodes using API3’s Airnode technology. This direct connection reduces costs, increases transparency, and potentially improves data quality since it comes straight from the source. The governance system allows token holders to curate data feeds and manage the network. API3 works particularly well when you want data directly from authoritative sources.
Pyth Network: High-Frequency Financial Data
Pyth Network specializes in high-frequency financial data, which is exactly what sophisticated trading applications need. Traditional oracle networks update prices every few minutes; Pyth provides sub-second updates by aggregating data from major trading firms, market makers, and exchanges. If you’re building perpetual futures, options protocols, or anything requiring extremely current market data, Pyth delivers what slower oracles can’t.
Tellor: Custom Data Queries
Tellor offers a unique pull-based oracle where data reporters stake tokens and compete to provide information. Users request specific data, reporters submit answers with stake backing their claims, and disputes can challenge incorrect data. The economic incentives align well for custom data queries that other oracles don’t support. Tellor shines for less frequent updates or niche data needs.
Chronicle Protocol: Security-Focused Transparency
Chronicle Protocol focuses on security and transparency for DeFi price feeds, employing validator-driven oracles with cryptographic verification. It’s gained adoption among projects prioritizing security audits and transparent data provenance.
| Oracle Provider | Best For | Key Strength | Supported Chains | Average Cost |
| Chainlink | General-purpose, high-security applications | Most established, comprehensive services | 15+ including Ethereum, BSC, Polygon, Avalanche, Arbitrum | Medium-High (Data Feeds sponsored, VRF costs $5-10) |
| Band Protocol | Cost-sensitive projects, frequent updates | Low fees, fast updates | 20+ via Cosmos IBC | Low-Medium |
| API3 | First-party data requirements | Direct API provider integration | 10+ including Ethereum, Polygon, Avalanche | Medium |
| Pyth Network | High-frequency trading, DeFi derivatives | Sub-second price updates | 40+ including Solana, EVM chains | Low-Medium |
| Tellor | Custom data queries, niche information | Flexible request system | 10+ including Ethereum, Polygon | Variable |
| Chronicle Protocol | DeFi protocols prioritizing transparency | Validator-based security | Ethereum, L2s | Medium |
Practical Steps: How to Use Oracles in Blockchain Development
You don’t need theory here — you need a build plan.
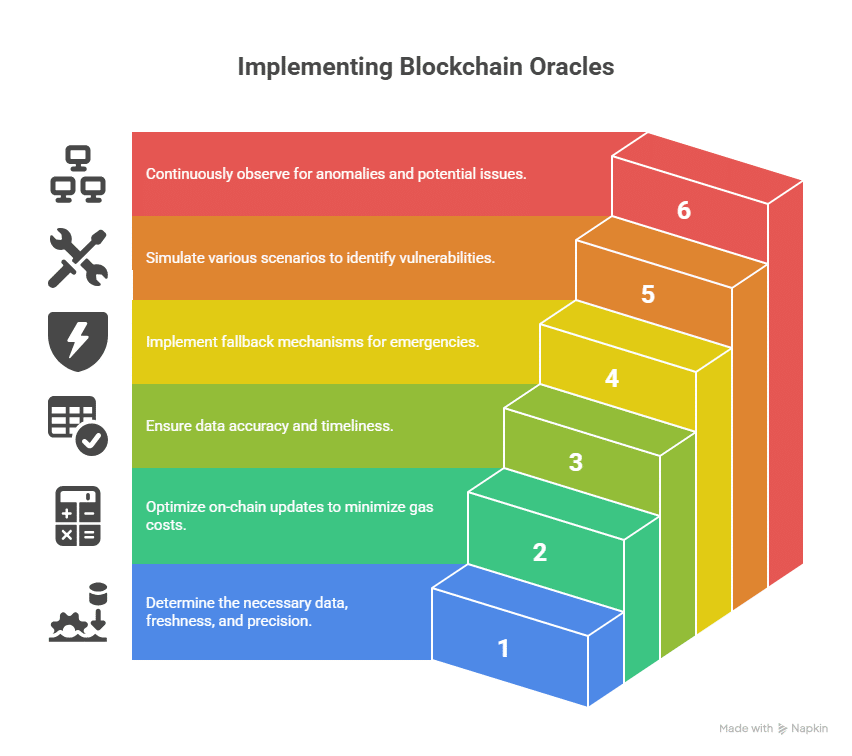
1) Pin down the data
What do you need? How fresh must it be? What precision? A lending protocol might want updates every minute; a rainfall trigger might settle once per day.
2) Design for cost
Every on-chain update costs gas. Cache values if several functions use the same reading. Batch work when you can. Keep hot paths cheap.
3) Validate everything
Refuse nonsense. If a stablecoin price shows $1.42, reject it. If a feed hasn’t updated within your time window, block actions that depend on it.
4) Plan for failure
Add circuit breakers, pause routes, and manual overrides for emergencies. If the primary feed dies, switch to a fallback with clear recorded governance.
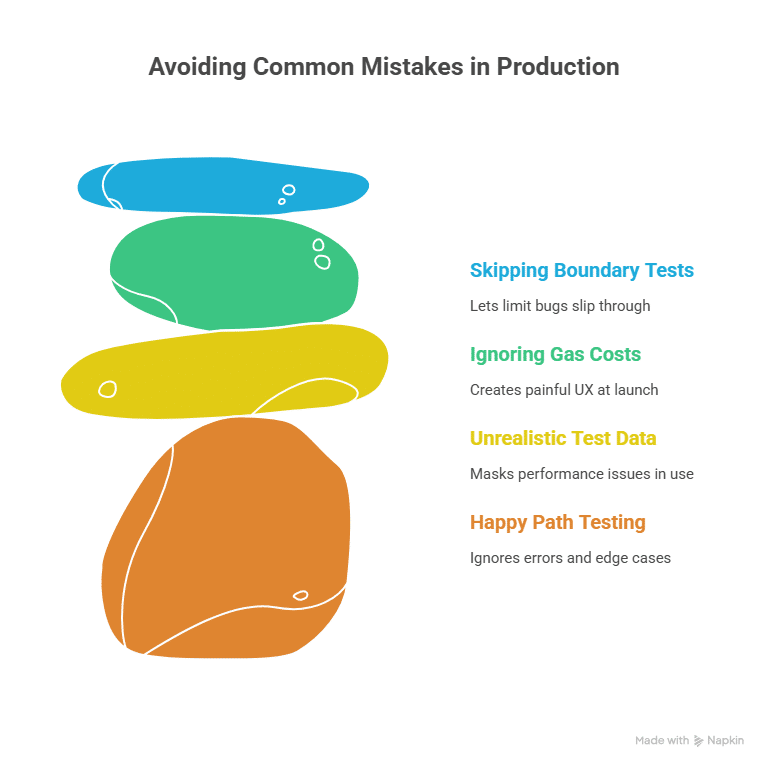
5) Test like a pessimist
Simulate stale data, zero values, spikes, slow updates, and timeouts. Fork a mainnet, read real feeds, and try to break your own assumptions.
6) Monitor in production
Alert on stale updates, weird jumps, and unusual cadence. Many disasters arrive with a small warning you can catch.
Step-by-Step Oracle Integration in Solidity
Let’s get hands-on with a step-by-step integrate oracle in Solidity tutorial. I’ll show you how to implement smart contract external data oracles using Chainlink, walking through a complete example.
Getting Your Environment Ready
First, you’ll need a proper development setup. Install Node.js, then initialize a Hardhat project. Install the Chainlink contracts package:
npm install –save @chainlink/contracts
Grab some testnet ETH from a faucet for the network you’re targeting. Sepolia is currently recommended for Ethereum testing.
Creating Your First Oracle Consumer
Here’s a practical contract that fetches ETH/USD prices. Notice how we’re importing the Chainlink interface and setting up the aggregator:
// SPDX-License-Identifier: MIT
pragma solidity ^0.8.19;
import “@chainlink/contracts/src/v0.8/interfaces/AggregatorV3Interface.sol”;
contract TokenPriceConsumer {
AggregatorV3Interface internal priceFeed;
constructor(address _priceFeed) {
priceFeed = AggregatorV3Interface(_priceFeed);
}
function getLatestPrice() public view returns (int) {
(
uint80 roundId,
int price,
uint startedAt,
uint updatedAt,
uint80 answeredInRound
) = priceFeed.latestRoundData();
require(price > 0, "Invalid price data");
require(updatedAt > 0, "Round not complete");
require(answeredInRound >= roundId, "Stale price");
return price;
}
function getPriceWithDecimals() public view returns (int, uint8) {
int price = getLatestPrice();
uint8 decimals = priceFeed.decimals();
return (price, decimals);
}The validation checks are crucial. We’re verifying that the price is positive, the round completed, and we’re not receiving stale data. These simple checks prevent numerous potential issues.
Implementing Request-Response Patterns
For randomness and custom data requests, you’ll use a different pattern. Here’s how VRF integration works:
import “@chainlink/contracts/src/v0.8/VRFConsumerBaseV2.sol”;
import “@chainlink/contracts/src/v0.8/interfaces/VRFCoordinatorV2Interface.sol”;
contract RandomNumberConsumer is VRFConsumerBaseV2 {
VRFCoordinatorV2Interface COORDINATOR;
uint64 subscriptionId;
bytes32 keyHash;
uint32 callbackGasLimit = 100000;
uint16 requestConfirmations = 3;
uint32 numWords = 2;
uint256[] public randomWords;
uint256 public requestId;
constructor(uint64 _subscriptionId, address _vrfCoordinator, bytes32 _keyHash)
VRFConsumerBaseV2(_vrfCoordinator)
{
COORDINATOR = VRFCoordinatorV2Interface(_vrfCoordinator);
subscriptionId = _subscriptionId;
keyHash = _keyHash;
}
function requestRandomWords() external returns (uint256) {
requestId = COORDINATOR.requestRandomWords(
keyHash,
subscriptionId,
requestConfirmations,
callbackGasLimit,
numWords
);
return requestId;
}
function fulfillRandomWords(
uint256 _requestId,
uint256[] memory _randomWords
) internal override {
randomWords = _randomWords;
}This two-transaction pattern (request then fulfill) is standard for operations requiring computation or external processing.
Integrating Oracle Data into Business Logic
Once you can fetch oracle data, integrate it into your application’s core functions. Here’s an example for a collateralized lending system:
function calculateLiquidationThreshold(
address user,
uint256 collateralAmount
) public view returns (bool shouldLiquidate) {
int ethPrice = getLatestPrice();
require(ethPrice > 0, “Cannot fetch price”);
uint256 collateralValue = collateralAmount * uint256(ethPrice) / 1e8;
uint256 borrowedValue = borrowedAmounts[user];
uint256 collateralRatio = (collateralValue * 100) / borrowedValue;
return collateralRatio < 150; // Liquidate if under 150%Testing Your Implementation
Deploy to testnet and verify everything works. Use Chainlink’s testnet price feeds, available on their documentation. Test edge cases systematically:
- What happens during price volatility?
- How does your contract behave if oracle updates are delayed?
- Does your validation catch obviously incorrect data?
- Are gas costs reasonable under various network conditions?
Only after thorough testnet validation should you consider mainnet deployment.
Best Practices for Production Oracle Integration
Implementing oracle services smart contract integration for production requires following established security and efficiency patterns.
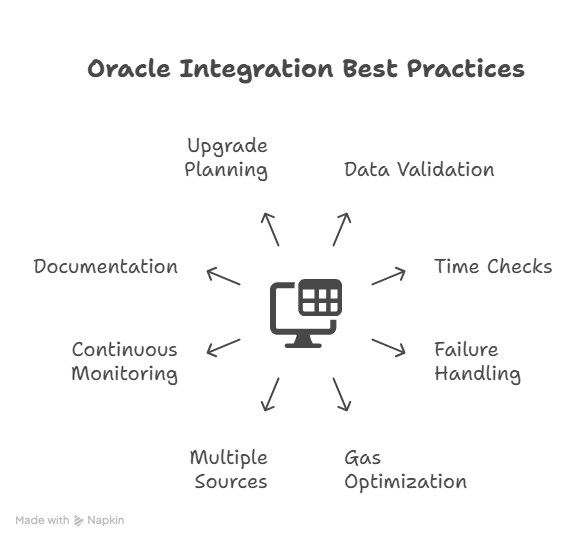
Validate Everything
Never assume oracle data is correct. Always implement validation logic that checks returned values against expected ranges. If you’re querying a stablecoin price, flag anything outside $0.95 to $1.05. For ETH prices, reject values that differ by more than 10% from the previous reading unless there’s a clear reason for such movement.
Implement Time Checks
Stale data causes problems. Always verify the timestamp of oracle updates. Set maximum acceptable ages based on your application’s needs. A high-frequency trading application might reject data older than 60 seconds, while an insurance contract might accept hours-old information.
Design for Failure
Oracles can and do fail. Your contracts must handle this gracefully rather than bricking. Include administrative functions allowing trusted parties to pause contracts or manually override oracle data during emergencies. Implement automatic circuit breakers that halt operations when oracle behavior becomes anomalous.
Optimize for Gas
Oracle interactions cost gas. Minimize calls by caching data when appropriate. If multiple functions need the same oracle data, fetch it once and pass it around rather than making multiple oracle calls. Use view functions whenever possible since they don’t cost gas when called externally.
Consider Multiple Data Sources
For critical operations, query multiple oracles and compare results. If you’re processing a $1 million transaction, spending extra gas to verify data with three different oracle providers is worthwhile. Implement median calculations or require consensus before proceeding with high-value operations.
Monitor Continuously
Set up monitoring infrastructure that alerts you to oracle issues. Track update frequencies, data ranges, and gas costs. Anomalies often signal problems before they cause disasters. Services like Tenderly and Defender can monitor oracle interactions and alert you to irregularities.
Document Dependencies Thoroughly
Maintain clear documentation of every oracle dependency: addresses, update frequencies, expected data formats, and fallback procedures. Future maintainers need to understand your oracle architecture to safely upgrade or troubleshoot systems.
Plan for Upgrades
Oracle providers evolve, and you may need to switch providers. Use proxy patterns or similar upgrade mechanisms, allowing you to change oracle addresses without redeploying core contract logic. This flexibility proves invaluable as the Oracle landscape develops.
Real Implementations That Rely on Oracles
- DeFi: lending and perps lean on robust price feeds to size collateral, compute funding, and trigger liquidations.
- Prediction markets: outcomes for elections, sports, and news settle through verifiable reports.
- Parametric insurance: flight delays and weather thresholds pay out without claims handling.
- Supply chain: sensors record temperature, shock, and location; contracts release funds only for compliant shipments.
- Gaming/NFTs: verifiable randomness keeps loot, drops, and draws fair.
- Cross-chain: proofs and messages confirm events on one network and act on another.
- Carbon and ESG: industrial sensors report emissions; markets reconcile credits on-chain.
Conclusion
Blockchain oracle development is the hinge that lets smart contracts act on real facts. Start by sizing the blast radius: when data touches balances or liquidations, use decentralized feeds, aggregate sources, enforce time windows, and wire circuit breakers. Choose providers by fit—Chainlink for general reliability, Pyth for ultra-fresh prices, Band for cost and cadence, API3 for first-party data, Tellor for bespoke queries, Chronicle for auditability.
Then harden the pipeline: validate every value, cap staleness, cache to save gas, and monitor for drift in cadence, variance, and fees. Finally, plan for failure with documented fallbacks and upgradeable endpoints, and test on forks until guards hold. Move facts on-chain without central choke points, and your dApp simply works.
Frequently Asked Questions
What is a blockchain oracle, in one line?
A service that delivers external facts to smart contracts in a way every node can verify.
Centralized vs decentralized — how to choose?
Match to value at risk. High-value money flows need decentralised, aggregated feeds. Low-stakes features can run on simpler sources.
Which provider fits most teams?
Chainlink is the broad, battle-tested default. Use Pyth for ultra-fast prices, Band for economical frequency, API3 for first-party data, Tellor for custom pulls, and Chronicle when auditability is the top ask.
Can oracles be manipulated?
Yes. Reduce risk with decentralisation, validation, time windows, circuit breakers, and multiple sources for important calls.
How should I test before mainnet?
Deploy to a testnet, use the provider’s test feeds, and force failures: stale rounds, delayed updates, and absurd values. Ship only after your guards catch every bad case.
Glossary
- Blockchain oracle development: engineering the bridge between off-chain data and on-chain logic.
- Oracle problem: getting outside data without recreating central points of failure.
- Inbound / Outbound: direction of data relative to the chain.
- Data feed: regularly updated values, usually prices.
- Consensus-based oracle: aggregates many sources to filter errors.
- VRF: verifiable randomness for fair draws.
- TWAP: time-weighted average price; smooths short-term manipulation.
- Circuit breaker: pauses risky functions when conditions look wrong.
Summary
Blockchain oracle development is now core infrastructure. The guide explains why blockchains cannot call external APIs and how oracles bridge that gap without creating a single point of failure. It outlines oracle types, including software, hardware, inbound, outbound, consensus, and compute-enabled models. It compares centralized speed with decentralized resilience and advises matching the design to the value at risk. It reviews major providers: Chainlink for broad coverage, Band for low cost, API3 for first-party data, Pyth for ultra-fast prices, Tellor for custom queries, and Chronicle for transparent DeFi feeds. It then gives a build plan: define data needs, control gas, validate values and timestamps, add circuit breakers and fallbacks, test for failure, and monitor in production. Solidity examples show price feeds and VRF patterns. Real uses include DeFi, insurance, supply chains, gaming, cross-chain messaging, and ESG data. The takeout is simple: design the oracle layer with safety first, since user funds depend on it.
Read More: Blockchain Oracle Development: A Complete Guide for Smart Contract Integration">Blockchain Oracle Development: A Complete Guide for Smart Contract Integration